Hi there,
This article will walk you through the “BlueSky Ransomware Blue Team Lab” lab from cyberdefenders.org.
I assume all the required files have been downloaded along with the listed tools as this post wont cover the same and we will directly jump into solving the challenges
Q1. Can you identify the source IP responsible for potential port scanning activity?
I started up opening the .pcap file on Network miner which listed all the involved IPs and amongst those one i believe is for Gateway, next was victim server ip while the other is attackers. The same can be viewed in Wireshark aswell, look for IP which is sending lot of packets on different ports and that’s our attacker IP
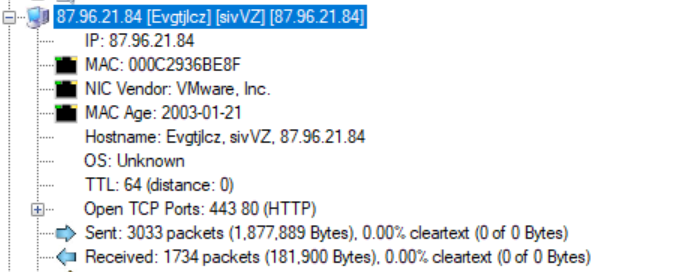
Q2. Can you identify the targeted account username?
Credentials and Username tried can be easily checked under ‘credentials tab’ on network miner tool.
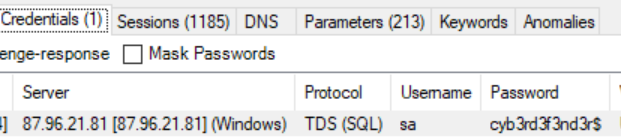
Q3. Can you provide the correct password discovered by the attacker?
Q3 and Q2 are same
Q4. What setting did the attacker enable to control the target host further and execute further commands?
We have to look into Event Viewer file (.evtx) for this flag. The scenario wants us to find the command executed by attacker to initiate the foot hold which can be easily checked under activities of ‘MSSQLSERVER’ inside Event Viewer window.
Be First to Comment